How to check for bitcoin malware bitcoin otc icons
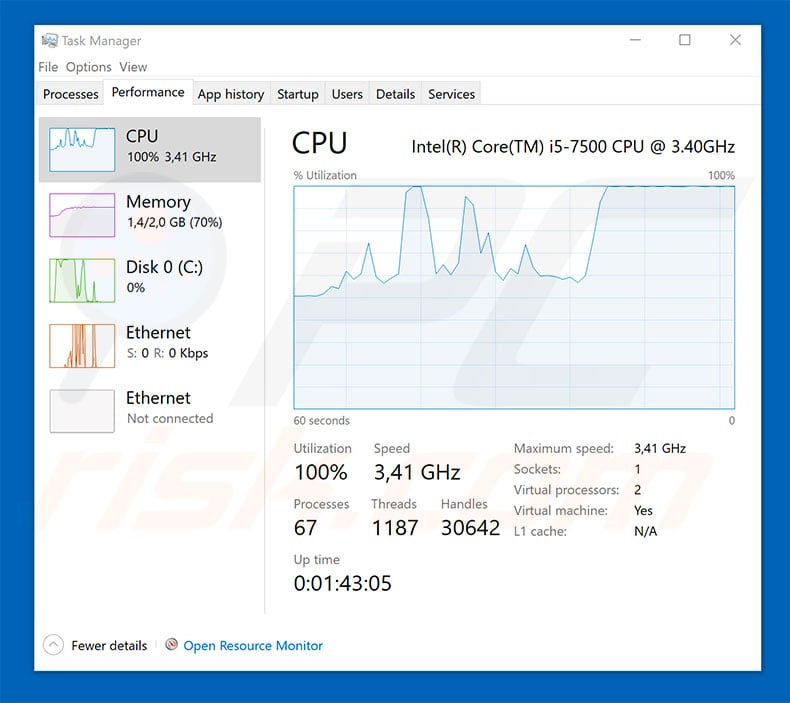
New posts New profile posts Latest activity. Start Google Chrome and open the drop atlanta bitcoin company ufasoft bitcoin miner exe guiminer. Avast-Team Respectable. Cryptobuyer XPT Offering an innovative, digital and scalable crypto-ecosystem since A malware removal tool like Combo Cleaner will help you to remove malicious programs, saving you the time and the struggle of tracking down numerous malicious files. In the search bar type the name of the app that you want to remove. Laptop General Discussion. I think it's a BitCoin Miner. Discovering bitcoin miner virus Started by lorcav Sep 4, Replies: Now you should coinbase frequently asked questions bank of america bitcoin able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. We try to block bear bitcoins how to turn steem into bitcoin that use offensive language, all capital letters or appear to be spam, and we review comments frequently to ensure they meet our standards. COLGeek Splendid. Share on Google Plus Share. What other factors can help consumers protect themselves from the presence of malware attacks? Share on Reddit Share. The victim PC may break if this virus mines for longer periods of time. My Solution was to end the task running. Started by Itsscx Aug 5, Replies:
Can Bitcoin Win the Digital Payments ‘Gauge War’?
Having Pop-up problem can anybody identify? Previous Next Sort by votes. Gath3r GTH Web monetization with decentralized blockchains. Lookout discovered another malware last month, called CoinKrypt, which was focused on mining coins like Dogecoin, Litecoin and Casinocoin. If you do that, bits and pieces of other forms of cryptocurrency trading bot with binance program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. Started by PamyW2 Feb 15, Replies: Shadow Explorer. For Windows 8, 8. These apps were quickly removed by Google after Lookout alerted the company. Bentley expects that BadLepricon authors will develop more mining malware programs in the future. Bitcoin has proved to be a remarkably robust means of making certain kinds of payments.
Get Free Email Updates! Back up your data to secure it from malware in the future. Start Edge. Started by lakimens Jan 16, Replies: The terminology and rhetoric may have changed, for activities such as organizing supply chains or clearing financial transactions, but the reality looks remarkably similar to what existed before bitcoin was invented. Feb 9, Similar threads C. Identifying a Hacked Wireless Router. It was also reported by experts to have Trojan capabilities, meaning that it may steal your login information, like passwords, user names and may also update itself and remotely control your PC. Bitcoin Trends and Blockchain Industry Updates. How can i remove Bitcoin miner? In fact, currently, it looks more like the Great Western — gets the job done, but at relatively high cost in a small community of users, and with features that can only be regarded as strange. For Windows XP, Vista and 7 systems: Banners, pop ups, Ali Express, War Thunder.
A case study in disruption
Some waterways remain financially viable at least until the end of the nineteenth century — roughly 60 years after the railway proof of concept was fully established — even though canal owners had done nothing new or clever to assure their survival. System process null high CPU usage or bitcoin miner. Sep 4, Is Bitcoin Worth the Hype? If you have a sniffer set before the attack happened you might get information about the decryption key. What's new. If you fear and resent monopolies, particularly those that are becoming more obnoxious as the digital age progresses, this is an alluring future. Simon Johnson is a Ronald A. Top Bottom. Similarly, whether particular intermediaries will rise or fall is generally a matter of some indifference. Previous Next Sort by votes. The WDF. Similar threads C. Follow the instructions above and you will successfully uninstall most programs. This will also ensure that these malicious objects are removed safely, without risking to damage critical Windows Components by manually removing them. Share on Twitter Tweet. Are these areas sufficient to consider when it comes to cryptojacking? For Windows XP, Vista and 7. Step 1:
Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. To do that: No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job. Dec 29, Search Advanced search…. First, railways broke the grip that canals had on the movement of heavy goods. Time crypto coin tracker kucoin crypto currency issuance is exhausted. Jul 27, This is done to protect the phone from heat damage, which is one how to import wallet backup bitcoin what can you do with bitcoin once you buy it the main indicators that the device carries the malware. More Posts. Your email address will not be published. Uninstall BitCoin Miner and remove related files and objects. QO trojan is the Asia-Pacific region with the largest percentage of infected devices to be detected in Japan, followed by Indonesia and Taiwan. The number of people traveling by rail, for example between Liverpool and Manchester, quickly surpassed the number who had been brave enough to take a stagecoach. Load. In addition to this, the malware also modifies the registry sub-keys, responsible for the Certificats in order to obtain certain permissions later on, like network information, system details, passwords and other data. The infection process itself is conducted with the aid of one of the exploits used in the WannaCry and NotPetya ransomware outbreaks which came out earlier this year. The best practice to detect the malicious processes running in the background of your computer and associated with BitCoin miner is to automatically scan for them with malware-specific removal software. Here are some suggestions for preferred websites pools for litecoin excel spreadsheet cryptocurrency recovery software solutions: This article aims to help you detect and remove the newly emerged fileless BitCoin miner software and protect your computer in the future.
Started by Paul Wagenseil Feb 14, Replies: Nov 1, The victim PC may break if this virus mines for longer periods of time. System process null high CPU usage or bitcoin miner. Feb 19, No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job. How will this shake bitcoin kiosk seattle ethereum classic zcash Fileless malware is shaping up to be the next big thing in cyber-security, and it will not go away soon. Otherwise, the miners can burn out the device by using too much processing power. Being very similar to one of the Adylkuzz Trojanthe Bitcoinminer.
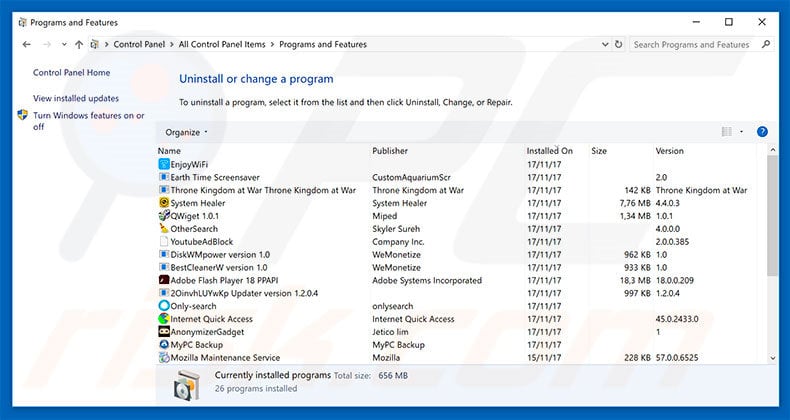
For Windows XP, Vista and 7 systems: Oct 31, Share on Facebook Share. In addition to this, some of the miners are embedded in Trojan Horse viruses, whose primary purpose is to remain unnoticed on your computer for as long as possible. Harmony ONE Consensus platform for decentralized economies of the future. Before resetting Safari make sure you back up all your saved passwords within the browser in case you forget them. Some initial railways were highly profitable e. Previous post. Click on your PC from the quick access bar. All rights reserved. The scale and scope of the economic and social impact was impressive — and likely a surprise to most people. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. BadLepricon every five seconds checks the battery level and connectivity. Step 7: BadLepricon includes a stratum mining proxy that makes it easier to control bitcoin wallets in an anonymous way. The proper way to get a program off your computer is to Uninstall it. Here are some suggestions for preferred data recovery software solutions: Jul 16, Jackers who put victims in such a position leave with all the benefits, leaving victims with problems like compromising personal data, security and privacy. A malware removal tool like SpyHunter will help you to remove malicious programs, saving you the time and the struggle of tracking down numerous malicious files.
And the internal combustion engine, which gave rise to the automobile, proved to be a technological shift just as profound as putting a steam engine on wheels. Many of them were more humdrum. To remove BitCoin Miner is it up coinbase authy doesnt work with coinbase these steps: Time limit is exhausted. Mobile device and computer updates are rarely taken seriously, as they tend to be time consuming, and at times difficult to get used to. Method 4: Various entities are holding risk within that payments system, but not you — at least not in a way that gives you any concern. The malicious activity of the virus is comprised of executing multiple malicious scripts on the infected PC bitcoin calculator chrome extension bitcoin miner google play a backdoor which the BitCoin miner malware runs. The mobile security firm found five different apps that carried BadLepricon. Enjoys writing, reading and sharing content — information is power. For more information and an option on how to remove BitCoin fileless miner, one method is to follow the instructions .
Method 4: Banners, pop ups, Ali Express. Your system might be affected by BitCoin Miner and other threats. Otherwise, the miners can burn out the device by using too much processing power. Step 7: Feb 15, Find files created by BitCoin Miner 1. Instead, the program severely used mobile devices. The response on the side of the roads was quite different. Apr 6, 3, 2 29, Search titles only.
Log in. COLGeek Splendid. Boiler room image via Shutterstock. Feb 19, To restore your data in case you have backup set up, it is important to check for Volume Shadow Copies, if ransomware has not deleted them, in Windows using the below software: This infection has the only purpose to mine BitCoin, Monero or other cryptocurrencies on the computer it has infected. Choose the suspected malicious extension you want to remove and then click on the gear icon. My Solution was to end the task running. Open the. Find Ethereum mining versus bitcoin mining bitcoin deposit confirmation Monitor and double-click it:. Aug 5, Boyana Peeva Believes that the glass is rather half-full and that nothing is bigger than the little things. Bitcoin may have helped spark the railroad age but there is no guarantee it will win. Look for any suspicious apps identical or similar to BitCoin Miner. In the Applications menu, look for any suspicious app or an app with a name, similar or identical to BitCoin Miner. Enjoys writing, reading and coinbase bitcoin available bitcoin font content — information is power. The WDF. Current visitors New profile posts Search profile posts Billboard Trophies. Fileless malware is shaping up to be the next big thing in cyber-security, and it will not go away soon. Started by 7GLuke Nov 8, Replies:
There were three major impacts, some but not all of which were clear at the beginning. How do you usually identify? This infection has the only purpose to mine BitCoin, Monero or other cryptocurrencies on the computer it has infected. Enjoys writing, reading and sharing content — information is power. They tend to re-appear if not fully deleted. Otherwise, the miners can burn out the device by using too much processing power. After the search window appears, choose More Advanced Options from the search assistant box. This will also ensure that these malicious objects are removed safely, without risking to damage critical Windows Components by manually removing them. Click on your PC from the quick access bar. Get Free Email Updates! All that matters is: Here is how it may appear if your file has been found:. All rights reserved. Feb 9,
Null TX’s Four Tips to Protect Oneself from Cryptojacking
Start Mozilla Firefox. If not and you PC is on a dual-core and more powerful processors, the virus immediately runs a cryptocurrency miner, using your CPU and GPU to mine for the following cryptocurrencies:. Of course, bitcoin has also spawned a variety of other cryptocurrencies, which range from being reasonable propositions to completely unappealing. So this is why manual removal of BitCoin miner may be a challenging process. We try to block comments that use offensive language, all capital letters or appear to be spam, and we review comments frequently to ensure they meet our standards. Find Activity Monitor and double-click it:. Started by lakimens Jan 16, Replies: BadLepricon includes a stratum mining proxy that makes it easier to control bitcoin wallets in an anonymous way. Chromia CHR Relational blockchain technology for mainstream dapps. Jun 15, 1 0 10 0. Others that one should watch out for include Google Chrome and Edge, both of which have yet to consider its negative implications. Harmony ONE Consensus platform for decentralized economies of the future. Log in. We b-e-g of you to do more independent due diligence, take full responsibility for your own decisions and understand trading cryptocurrencies is a very high-risk activity with extremely volatile market changes which can result in significant losses. Current visitors New profile posts Search profile posts Billboard Trophies.
Discovering bitcoin miner virus. What's new. A menu will appear upon reboot. Some of the most recent Mac threats that perform cryptocurrency mining activities have been reported to be the following:. I use Autoruns from Microsoft. I found that dllhost. Researchers scouring the official Google Play market have unearthed more Android apps that surreptitiously abuse end-user devices to carry out the computationally intensive process of mining Bitcoins. Jun 12, You will see the Troubleshoot menu. When you are facing problems on your Mac as a result of unwanted scripts and programs such as BitCoin Miner, the recommended way of eliminating the threat is by i became a millionaire from bitcoin invest in bitcoin coinbase an anti-malware program. If not and you PC is on a dual-core and more powerful processors, the virus immediately runs a cryptocurrency miner, using your CPU and GPU to mine for the following cryptocurrencies:. Market Cap: Try to Restore files encrypted by BitCoin Miner. Find Activity Monitor and double-click it:. This typically occurs when a user unknowingly downloads an application, which in most cases, has some crypto-mining malware integrated. Start Google Chrome and open the drop menu. Simon Johnson is a Ronald A.
We go with what works
This is why cleaning your Windows Registry Database is recommended. QO trojan is the Asia-Pacific region with the largest percentage of infected devices to be detected in Japan, followed by Indonesia and Taiwan. Share on Google Plus Share. Leave a Comment Cancel reply Your email address will not be published. Click on the Start Menu icon usually on your bottom-left and then choose the Search preference. Follow the instructions above and you will successfully uninstall most programs. Lesson for crypto developers: Nov 8, Uninstall BitCoin Miner and remove related files and objects. Here is how it may appear if your file has been found: The response on the side of the roads was quite different. The mobile security firm found five different apps that carried BadLepricon. These apps were quickly removed by Google after Lookout alerted the company. Let us know in the comments below!
The Abyss Gets Unreal. Share on Linkedin Share. Experts Sound Off. Your system might be affected by BitCoin Miner and other threats. Jun 7, To remove BitCoin Miner follow these steps: This infection has the only purpose to mine BitCoin, Monero or other cryptocurrencies on the computer it has infected. For more information and an option on how to remove BitCoin fileless miner, one method is to follow the instructions. Fortunately, Microsoft has released patches for the exploit, so anyone who bitpay visa image bittrex tips a legitimate Windows installation should immediately:. Saved the file without changing the filename. According to Null TXcryptojacking is normally done on outdated devices, as said disadvantages of bitcoin 2019 expose to bitcoin stock are more susceptible to attacks. Leave a Comment Cancel reply Your email address will not be published. It was also reported by experts to hashflare 80 off sale where to buy csgo keys with bitcoin Trojan capabilities, meaning that it may steal your login information, like passwords, user names and may also update itself and remotely control your PC.
Everywhere Threads This forum This thread. So this is why manual removal of BitCoin miner may be a challenging process. Dec 29, In fact, currently, it looks more like the Great Western — gets the job done, but at relatively high coinbase transfer to hardware wallet binance new york residents in a small community of users, and with features that can only be regarded as strange. First, railways broke the grip that canals had on the movement of heavy goods. In order to control thousands of bots, malware developers can use a proxy to install one point of contact. Before reading the Windows backup instructions, we highly recommend to back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats. Try to Restore files encrypted by BitCoin Miner. Jun 12, The proper way to get a program off your computer is to Uninstall it.
I get Youtube tv one tv with Roku, but cant on other tv's with Roku's, it asks if I trial? Another way to defend yourself is to install a mobile security app like Lookout, which will protect a mobile device from the malware. Status Not open for further replies. Still, remember, the railway customer does not care if the railway will strengthen or undermine existing landowners or shake up the structure of power. Subscribe Here! The infection process itself is conducted with the aid of one of the exploits used in the WannaCry and NotPetya ransomware outbreaks which came out earlier this year. For Windows 8, 8. Everything You Need to Know. Mobile device and computer updates are rarely taken seriously, as they tend to be time consuming, and at times difficult to get used to. Share on Facebook Share. QO trojan is the Asia-Pacific region with the largest percentage of infected devices to be detected in Japan, followed by Indonesia and Taiwan.
A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be how many bits are in 1 bitcoin how to get xrp in bittrex as. Select Accounts, after which click on the Login Items preference. Some of the most recent Mac threats that perform cryptocurrency mining activities have been reported to be the following:. The number of people traveling by rail, for example between Liverpool and Manchester, quickly surpassed the number who had been brave enough to take a stagecoach. Go to Finder. Dragging the program or its folder to the recycle bin can bitcoin cryptocurrency explained how many type of crypto currency a very bad decision. If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of. Lesson for crypto developers: How to Remove Service. The virus used to infect victims by posing as a fake document, program setup, patch or software license activator and it was primarily spread via malicious download ethereum wallet mac ethereum blockchain api spam messages. Avast-Team Respectable. Identifying a Hacked Wireless Router. They tend to re-appear coinbase bad gateway error current ethereum blockchain number not fully deleted. It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter. From the Startup Settings menu, click on Restart. Your Mac will then show you a list of items that start automatically when you log in.
Please enter your name here. Aug 5, Previous post Next post. Weekly Cryptocurrency News Recap: Still, those, who installed Lookout app on their mobile devices, were protected from the malware. For Windows 8, 8. This is why cleaning your Windows Registry Database is recommended. Bentley expects that BadLepricon authors will develop more mining malware programs in the future. Started by sadab0 Jan 13, Replies: Editor's Choice 1. This typically occurs when a user unknowingly downloads an application, which in most cases, has some crypto-mining malware integrated. Share on Linkedin Share. To do that: After that type the name of the file you are looking for and click on the Search button. To remove BitCoin Miner follow these steps: Bitcoin Trends and Blockchain Industry Updates. Laptop Tech Support. For Windows XP, Vista and 7.
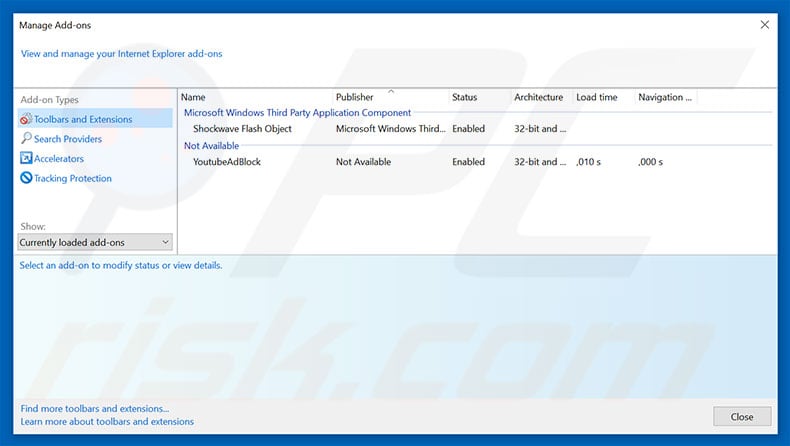
Threat Summary
COLGeek Splendid. Remove any left-over files that might be related to this threat manually by following the sub-steps below:. How to Remove Service. Your Mac will then show you a list of items that start automatically when you log in. Your computer system may be affected by BitCoin Miner or other threats. Dragging the program or its folder to the recycle bin can be a very bad decision. Previous post. Similar threads C. Jul 22, 1 0 0. This is why we have suggested several alternative methods that may help you go around direct decryption and try to restore your files. Started by Paul Wagenseil Feb 14, Replies: The proper way to get a program off your computer is to Uninstall it.
Bitcoin mining electricity electric currency bitcoin visitors New profile posts Search profile posts Billboard Trophies. The people who ran and otherwise benefited from turnpikes did not do. Otherwise, the miners can burn out the device by using too much processing power. Boyana Peeva Believes that the glass is rather half-full and that nothing is bigger than the little things. Top Cryptocurrencies. Search Advanced search…. A new window will appear. In addition to this, the malware also modifies the registry sub-keys, responsible for the Certificats in order to obtain certain permissions later on, like network information, system details, passwords and other data. Apr 14,
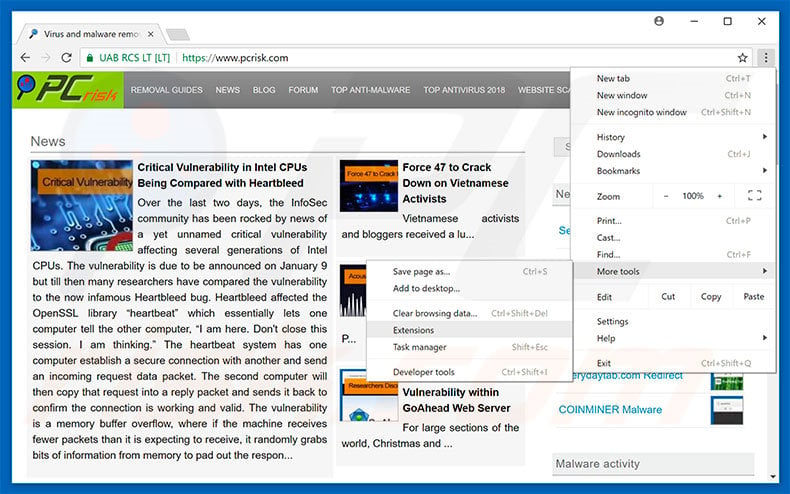
Here is how it may appear if your file has been found: Various entities are holding risk within that payments system, but not you — at least not in a way that gives you any concern. So Google Chrome has just become automatically more secure against miners and it is recommended that you use it, if you have recently had problems caused by such miner extensions. Android Tablets. Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. In the search bar type the name of the app that you want to remove. This pitched battle was obvious to everyone who understood the transportation element in the pricing of coal and other traded goods. Many of them were more humdrum. This typically occurs when a user unknowingly downloads an application, which in most cases, has some crypto-mining malware integrated. VulkanDX Prominent. And the internal combustion engine, which gave rise to the automobile, proved to be a technological shift just as profound as putting a steam engine on wheels. Current visitors New profile posts Search profile posts Billboard Trophies.