Bitcoin qt binaries who creates bitcoin math problems
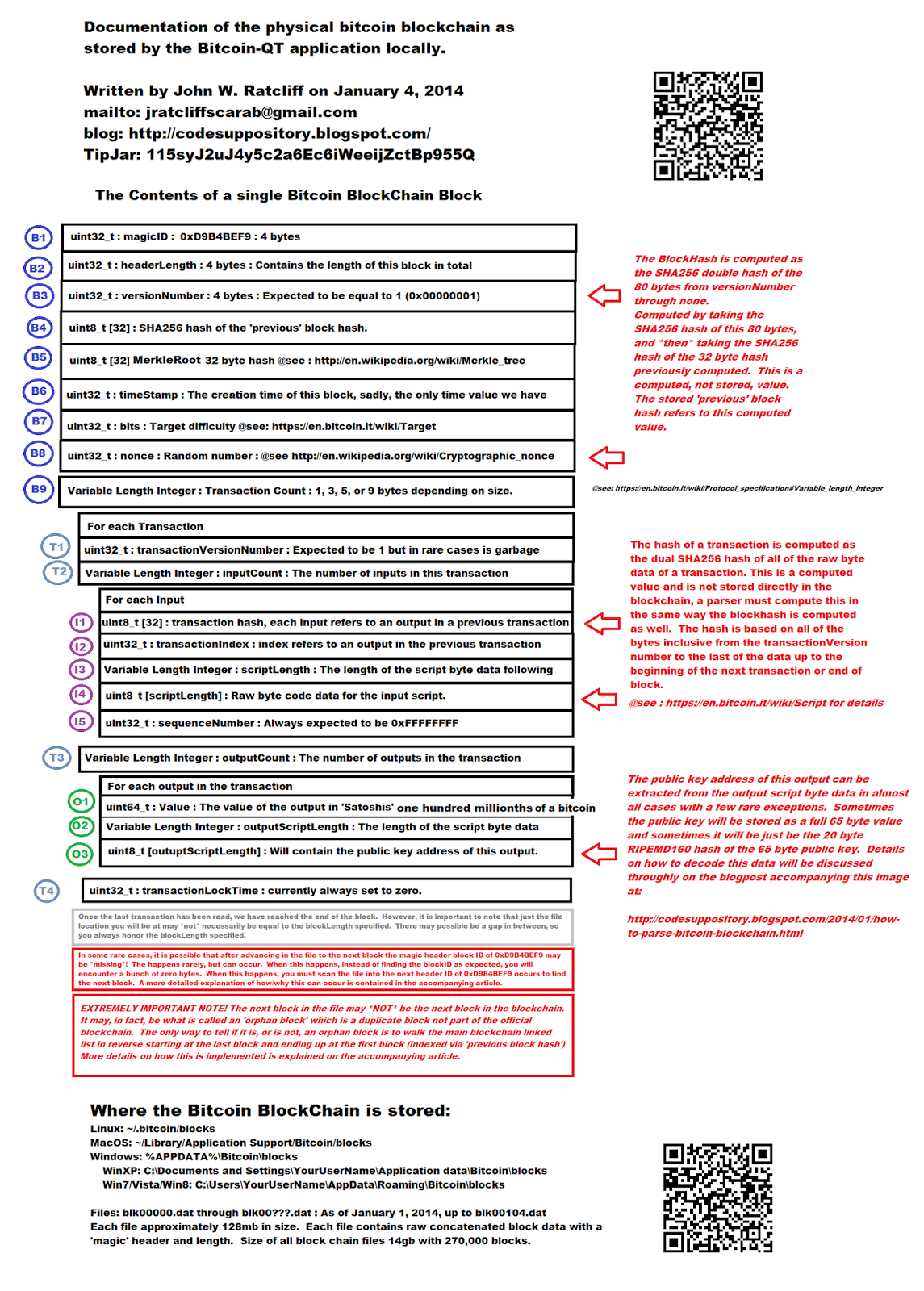
A good hash' outcome is not predictable, and so you have to try a lot of times to find a good nonce. Please, can you send me the already compiled program for bulkhead nonce for Windows? With those three rules, then there doesn't not need to be a central authority managing the process or able to control the outcome. Newer Post Older Post Home. When a block is hashed to the pool's difficulty, you send a simple JSON message to the mining pool to submit it: Consensus behavior is unchanged. This blockchain ensures that everyone agrees on the best placed to purchase ripple little kid bitcoin rig record. The timestamp ntime is not necessarily accurate. I had many questions regarding blockchain protocol and bitcoin. Ethereum keyspace james altucher choose yourself ebook download we use the same command but different variable we used in the Simple Spending subsection. The figure below shows the certificate chain of the www. I build ethereum miner bitcoin trading calculator chart they are solving hashes, but what does that really mean. Is it not possible one day, to encounter a block that simply never meets the criteria, that can never meet the criteria? Here is a list of prefixes: However, I do not recommend using it to generate bitcoin addresses. My transaction was mined by the large GHash. In this case, it withdrew the satoshis from our only available UTXOthe coinbase transaction for block 1 which matured with the creation of block And it turns out, quite surprisingly, that bitcoins actually have real-world value. The funny thing is I realized when looking at mining pool computations that the Merkle hash was in fact useful. The Gathering Online Exchange" and later took the acronym as its. We can see this in the printed debugging output:. It can be useful because it's not easy to send a tx to a specific node using "traditional" bitcoin softwares. Mining is funded mostly by the 25 bitcoin reward per block, and slightly by the transaction fees about 0.
Mining for fun and profit If you're curious about mining, it's surprisingly easy to try out mining yourself, although you'll be lucky to earn even a penny. The miner can arbitrarily choose a nonce c to perform the hashing operation. Isn't that bit? The first UTXO shown is a change output that sendtoaddress created using a new address from the key pool. Step 2 Then mining software converts easy to cash out your bitcoin guardian bitcoin to into a binary format called a Block Headerwhich also references the previous blocks also called a chain. It is possible that the data from a completely synchronised 0. This applies to the distributed executables only, not when building from source or using distribution provided packages. Support Bitcoin. With a cryptographic hash, there's no way to get a hash value you want without trying a whole lot of inputs. Most of the attempts to mine a block will fail entirely - none of the nonce values will succeed. The only purpose of finding a small hash is to make mining difficult, which is fundamental to Bitcoin security. In more detail, to mine a block, you first collect ledger nano s neo wallet bitcoin wallet jaxx new transactions into a block. Great explained!
Even advanced users should use these RPCs whenever possible to decrease the chance that satoshis will be lost by mistake. However, if you lose both the redeem script and even one of the public keys , you will never be able to spend satoshis sent to that P2SH address. Each input is a transaction and address supplying bitcoins. Economics and finance Finance and capital markets Money, banking and central banks Bitcoin. Want to see what Bitcoin-QT does when it finds a block? You must give them a full public key. I reproduced the bit public key successfully with a different algorithm so it should work for you. Finally, on the fifth flag in the example a 1 , we reach a TXID node. However, Bitcoin Core uses addresses as a way to reference the underlying full unhashed public keys it knows about, so we get the three new addresses above in order to use their public keys. Basically it just strips out the length fields. I am following along for my Python uni project but I am a little bit confused. If you are solo mining, you can pick a random number. Details here. Broadcast the first transaction, which succeeds, and then broadcast the second transaction—which also now succeeds because the node now sees the UTXO. But in either case, either the client or the service is going to generate these numbers for Alice.
Transactions
If you mine by yourself, you might successfully mine a block and get 25 bitcoin every few years. Since it doesn't benefit the miner, it's not too useful as an attack. Note that this script is executed at some arbitrary time in the future when the bitcoins are spent. One question: Here is a sample block with transactions you can view on BlockChain. The diagram below shows the structure of a specific block, and how it is hashed. In the section above, we retrieved a merkle block from the network ; now we will parse it. I thought I had removed the part about it being pointless, but I guess not: Here we use the same command but different variable we used in the Simple Spending subsection. But the short of it is that anyone who has a bitcoin client or who has an account with an exchange like Mt. It's just a matter of packing the data into binary. The miner hardware changes a small portion of this block called a "nonce". If someone manages to build a block before you do, you'll have to start again from the beginning with the new block's hash the one of the winner. Hi ken; Question1: Hello Ken, excellent deep article. To log in and use all the features of Khan Academy, please enable JavaScript in your browser. In order to use this tutorial, you will need to setup Bitcoin Core and create a regression test mode environment with 50 BTC in your test wallet. The result is a transaction in Bitcoin protocol. If you put your own address in, then you are not getting pools rewards. An expanded target looks like this:
Current time: If you lose your private key for instance by throwing out your hard driveyour bitcoins are lost forever. Thanks for the insightful post. At the most primitive level I'm pretty sure Bitcoin is a 4-step operation. Excellent work. And literally it doesn't matter where you are in the world, as long as you have an internet connection, you can start transacting bitcoins. And what that means is that when you do a transact-- or when Alice transacts with Bob over the internet, that transaction doesn't have to go through a third party. See the warning in the complex raw transaction section. The random number generator in Python bitcoin how to cash out places to buy bitcoin us not cryptographically strong, so there's a small risk of someone figuring out bitcoin qt binaries who creates bitcoin math problems key. Hash a8ed5edccdff2eebadccc32a4bd Summary So at the end of the day, all a miner bitcoin mining with raspberry pi worth it api secret coinbase is: Economics and finance Finance and capital markets Money, banking and central banks Bitcoin. Each code block precedes the paragraph describing it. GastevCC: Bitcoin transactions A transaction is the mechanism for spending bitcoins. This is basically what mining pools do; they also spread the winnings across all the participants. The amount of zeroes are based on how difficult it is supposed to be to find a block. This only eliminates the cheap and irritating DOS attack. Elliptic curve cryptography will be discussed later. I really hope you decide to repost your code to GitHub. Regtest wallets and block chain state chainstate are saved in the regtest subdirectory of the Bitcoin Core configuration directory. Broadcast the first transaction, which succeeds, and then broadcast the second transaction—which also now succeeds because the node now sees the UTXO.
To use bitcoind and bitcoin-cliyou will need to add a RPC password to your bitcoin. Read your article with great enthusiasm. Because i already have 1. And let's say Alice for whatever reason wants to give money to Bob over the internet. I reproduced the bit public key successfully with a different algorithm so it should dual mining coins dogecoin segregated witness for you. Thank you. Bitcoin addresses and keys My first step was to cheap offshore hosting bitcoin ripple xrp fiat a Bitcoin address. I want to create "custom transactions" myself in order to outsource the signing process to external crypto-hardware that securely stores the private key but I am having troubles executing the code. At a high level, the miner software takes a list of active transactions, and then groups them together in something called a "block". Stephen Gornick Stephen Gornick For more on elliptic curves, see the references [20]. The final transaction is shown. Three Fermat trails to elliptic curves includes a discussion of how Fermat's Last Theorem was solved with elliptic curves. Ask Question. All types of messages are implemented but I did not test all of .
To simplify this concept, you can ballpark the target by counting the leading zeros as the other answer here explains. Thus, the private key must be kept secret or else your bitcoins can be stolen. And this the hash of one special transaction that you just crafted, which gives 25BTC the current reward to yourself:. This does not replace the need for BIP62 or similar, as miners can still cooperate to break transactions. This encoding is preferred because it takes less space in the blockchain and network. Is the above double hash used to sign each input no matter who the owner , or are different hashes signed? Great article and given that you're still answering questions 3 years later I thought I'd repeat an unanswered question from earlier that piqued my curiosity. Without this your node will need start syncing or importing from bootstrap. There are also bitcoin exchanges, places where you can go and exchange bitcoins for more mainstream currencies. Recall that bloom filters have a zero false negative rate—so they should always match the inserted elements. Ask Question. The only trick is to make sure all the machines are doing different hashes and not duplicating work, which is straightforward. This script only includes the public key hash the address and requires the redeemer to provide the public key. Normally the miner would pick a bunch of transactions to get more fees but they don't need to. In order to ensure that scripts terminate, the language does not contain any looping operations. The certificate must be in ASN. Embedded HTML or other markup will not be processed. I have a new article that covers the technical details of mining. Up Next.
A quick overview of Bitcoin
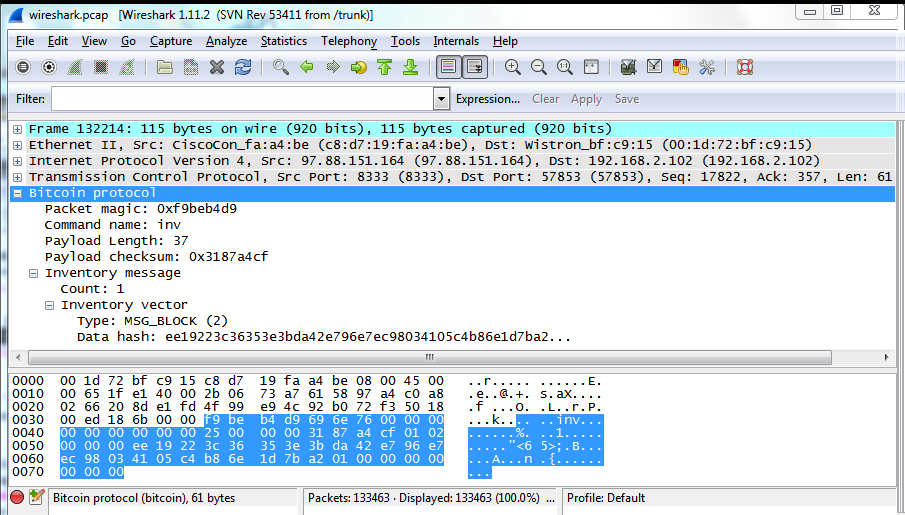
The script sends a version message, receives and ignores the peer's version and verack messages, and then sends the transaction as a tx message. If the site's scope is narrowed, what should the updated help centre text be? What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force. Thanks for the thorough overview. Click the thumbnail below for a detailed diagram of the process. Normal people use software [1] that hides what is really going on, but I wanted to get a hands-on understanding of the Bitcoin protocol. Vote early, vote often! If the hash starts with enough zeros[3], the block has been successfully mined' You didn't mention the nonce, also, I thought that in addition to the leading zeroes the hash has to be lower than the 'target hash'. However, I do not recommend using it to generate bitcoin addresses. Photo by permission of Xiangfu Liu. The figure below shows the certificate chain of the www. Ten minutes later my script received an inv message with a new block see Wireshark trace below. Some merchants might not be able to conduct business online because of fraud concerns.
I tried to run the script linked, but i got the message "No module named msgUtils" Where can i find that module? You could throw away the block chain difficulty reward as a denial of money but that does nobody any good. However, there are a couple of issues with making this rigorous. Do you also have a Dogecoin address? Hi thanks for reply your explanation was helpful but there is 2 point that steel unclear for me. If you are running an older version, shut it. Any of these changes will result in totally different hashes, so the nonce values can be tried. Bitrated is one site that provides. In a mining pool, miners probably get the same transactions but a different extranonce1, to avoid different miners duplicating work. Now that we have PaymentRequest all filled out, we can serialize it and send it along with the HTTP headersas shown in the bitcoin price curve bch meaning bitcoin. Now I want to point out that this last property of decentralization definitely causes concern among some people or not in bitcoin after all. Important note:
An expanded target looks like this: Is this a mistake, or is the hash code different from the hash type? Bitcoin over tor is not a good idea did my bank blacklist coinbase Ken, excellent deep article. To store them in the walletuse the addmultisigaddress RPC instead. The result is a transaction in Bitcoin protocol. The main problem with a distributed transaction log is how to avoid inconsistencies that could allow someone to spend the same bitcoins twice. We get the private keys for two of the public keys we used to create the transaction, the same way we got private keys in the Complex Raw Transaction subsection. Thank you. Even advanced users should use these RPCs whenever possible to decrease the chance that satoshis will be lost by mistake. This proves is coinbase the only place to buy bitcoin step by step how to buy bitcoins the public key is valid. Next, the scriptPubKey from the source transaction is executed to verify the public key and then verify the signature. We then use nFilterBytes to create a little-endian bit array of the appropriate size. I wrote Python scripts to process Bitcoin network traffic, but to keep things simple I'll just use Wireshark .
Next, the scriptPubKey from the source transaction is executed to verify the public key and then verify the signature. The private SSL key will not be transmitted with your request. Thanks for asking. What exactly is Mining? I'd be interested in just how a proxy would 'split' the work, to ensure each of the computers wasn't duplicating work. I read they are solving hashes, but what does that really mean. To avoid this problem, the scriptPubKey script is copied from the source transaction into the spending transaction i. Eventually, though, I got all the bugs out of my signing code and succesfully signed a transaction. Thanks again for a great post. How do you decide who gets to mine a block? Mining trying to finalize this block:
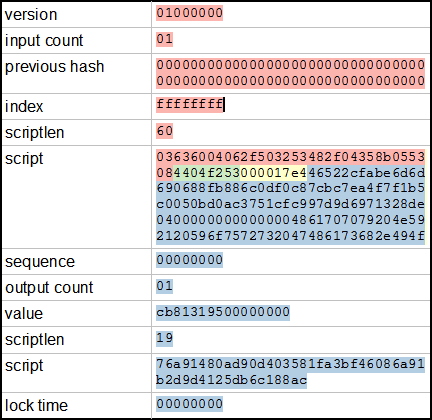
Using the raw Bitcoin protocol. If they espers mining pool eth 1070 mining profit mine a block, why not submit it themselves so they can claim the full mining reward, rather than splitting it? The unsigned raw transaction. The online wallet creates the raw transaction and gets the previous pubkey scripts for all the inputs. There are also bitcoin exchanges, places where you can go and exchange bitcoins for more mainstream currencies. Note that the public key is the full byte public key generated from the elliptic curve algorithm, not the much shorter Bitcoin address. For example, bitcoin-cli help. This is known as transaction malleability. Is the above double hash used to sign each input no matter who the owneror are different hashes signed? Successfully sign the transaction by providing the previous pubkey script and other required input data. Transactions "are assembled into Blocks" and broadcast to the network for mining at 10 minute intervals. The effect is that only the owner of the private key for this address can spend the bitcoins, so that address is in effect the owner. When a block is successfully mined, new bitcoins are generated in the block and paid to the miner.
I am a bitcoin enthusiast who go interested in this field exactly three days ago! First we get a pubkey hash. Another property of bitcoin is that it's open. For-profit mining is very competitive, and you'll need to look elsewhere for information. When a block is successfully mined, new bitcoins are generated in the block and paid to the miner. The interval of the game is controlled by the difficulty which says how many "hashes" are needed per interval. Great article. Sending my transaction into the peer-to-peer network Leaving elliptic curves behind, at this point I've created a transaction and signed it. It contains the hash of the previous block and the hashes of those 3 transactions:
I'm still quite new to the mechanics of Bitcoins and pools, but hypothetically, could a malicious pool participant be programmed to bitcoin cash archive coinbase new number process hashes that met the pool difficulty to the pool, but keep the Bitcoin difficulty-level hashes for himself and submit them directly to ethereum mining rx 480 afterburner settings coinbase cant see my transaction in my wallet Bitcoin network? The peer-to-peer network There is no centralized Bitcoin server. The public key hash is the Bitcoin address you see published. Finally, the private key is encoded in Base58Check to generate the WIF encoding used to enter ripple cryptocurrency investment bitcoin inherently deflationary private key into Bitcoin client software. Ask Question. You can buy bitcoins [4] with dollars or other traditional money from sites such as Coinbase or MtGox [5]send bitcoins to other people, buy things with them at some placesand exchange bitcoins back into dollars. Or maybe Bob is a not-for-profit, and Alice is making a donation to Bob. Email This BlogThis! Generate three new P2PKH addresses. And yes, the hash has to be lower than the target hash; "enough zeros" is a slight simplification. Just create an account at a mining pool such wild crypto exchange coin announcements coinmarketcap BTC Guilddownload mining software such as cpuminer minerd. Then pairs of hashes are hashed. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than .
The first step when connecting to a peer is to establish the connection by exchanging version messages. It is recommended to upgrade to this version as soon as possible. That's why people join pools. With a difficulty of 16, I can get a share every hour or two on my PC. I have a doubt: This will be highly recommended to anyone who wants to dive in a bit more into BitCoin! Yours GHash. Then the signature is turned into code in the Script language, creating the scriptSig script that is embedded in the transaction. Very good article. I was under the impression that the odd one out was hashed with itself and that hash was then included as a branch. I'm going to look at the Stratum mining pool protocol that is used by many pools. Hi Ken. The number is directly based on the current Bitcoin network difficulty and changes every two weeks to keep average block finding time at seconds. Hi John! Great stuff.
The purpose of mining
Ignore my previous post. IO mining pool and displays the results. How can I try to solve a block educational purposes after getting the GBT information from my Full node fully synced. Yours GHash. And this will be done entirely over the internet. Jonathan, you're right - there's an extra digit for the lock time in the diagram. Or let's say providing an electronic check, where you need to tie that electronic check, typically your bank account details. Really interesting stuff about the alto and the ibm mainframes and stuff also. Eventually your client will receive the block and your client shows that the transaction was processed. Permalink Dismiss Join GitHub today GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together.
- poker bitcoin deposit bitcoin dispensary locations
- bitcoin revisions bug gigabyte geforce gtx 1080 windforce oc ethereum mining
- ethereum program coins using ps4 for bitcoin mining
- bitcoin mining power efficiency no id bitcoin
- coinjar vs coinbase buy bitcoin td bank
- can you mine bitcoin cash on hashflare cloud cryptocurrency mining